Proxy Tab
This is the single most important tab in BurpSuite. The proxy tab allows you to monitor the flow of application traffic while making notes. I use several extensions such as 'Scope Monitor' which greatly help organize the content.
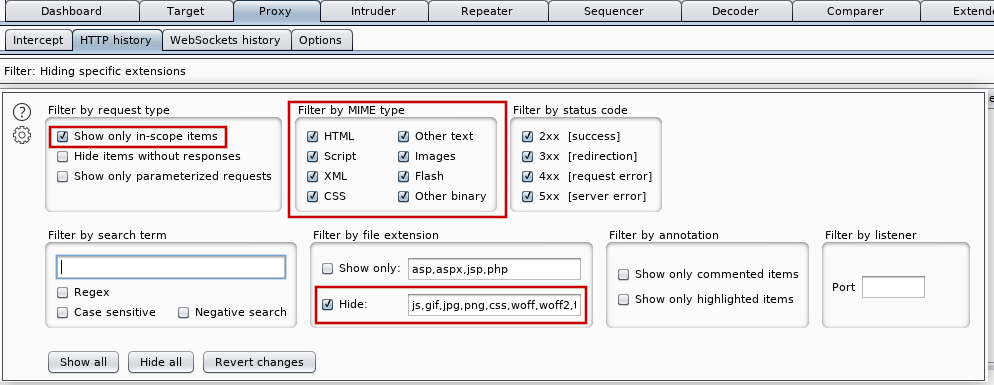
A common pitfall I see among junior application pentesters is failing to have the proxy filters setup to observe more traffic at the beginning of their engagement, often overlooking requests for binary content. I filter out and analyze JS in the 'target' tab, don't need it cluttering up my proxy tab. And I tend to only include requests in scope once that has been established after crawling the app.
Intruder
- You can send an item from Intruder directly to a Burp Scanner config to analyze one parameter
- Make sure you know how to use the different attack types. I use the 'pitchfork' attack type almost as much as the standard 'sniper' payload.
- Experiment with the Payload Processing, it's extremely useful for transforming data that you may feel needs to be scripted. This is quicker.
- Payload encoding is often an issue when dealing with wordlists of already encoded characters. May want to disable this upon monitoring Intruder data.
- Save your intruder scan results, you may forget to take a screenshot.
Repeater
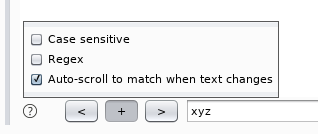
Check the 'auto-scroll to match when text changes' option to save yourself some time when hunting for reflected content.
You may need to disable Repeater options such as "Update Content-Length" when validating for issues such as HTTP Request Smuggling.
Templates
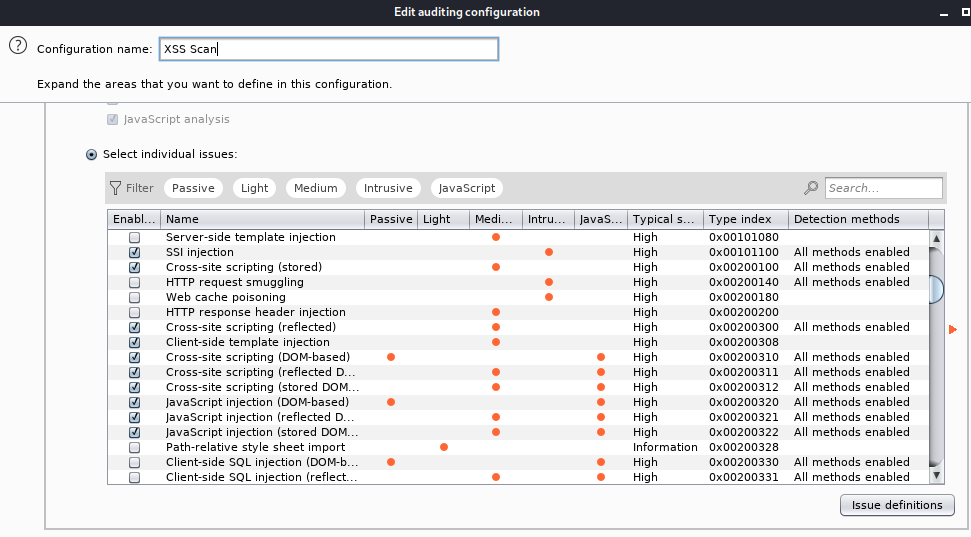
With the release of Burp 2.0 a wide range of templating options have become available. So far, I've created several scan profiles which I use when running my scans. For example, an XSS only profile is easily created.
Project Options
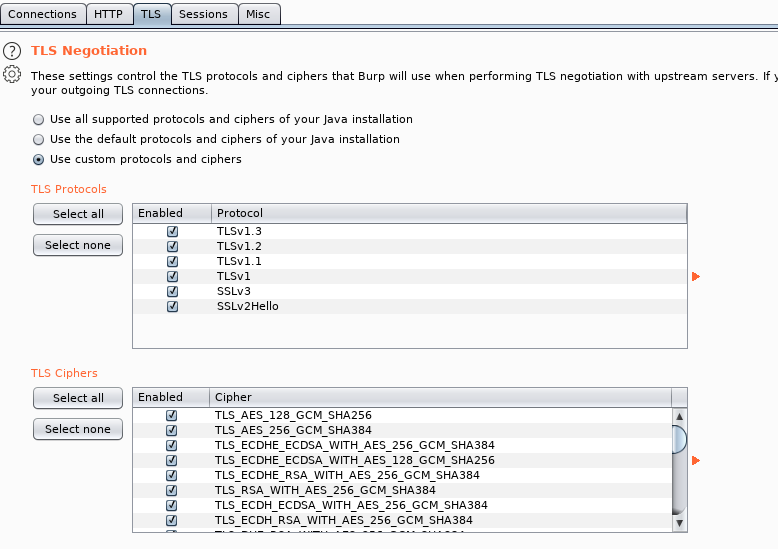
TLS: Select the 'use custom protocols and ciphers' and select everything in both lists. The reason we're doing this is to avoid TLS issues in the future with misconfigured middleware. Additionally, check the Unsafe renegotiation option.
Sessions: These are typically left default, until I understand the application more in detail and need additional macro's or cookie jar handling functionality (such as cookies -> scanner)
Misc: If your organization has a private burp collaborator server, fill it in here. Also, if you have internal proxy issues polling for Burp Collaborator over unencrypted HTTP will be your solution.
User Options
Typically I have a SOCKS Proxy setup to relay my burp traffic, but it's not always necessary depending on where you're executing your pentest from.
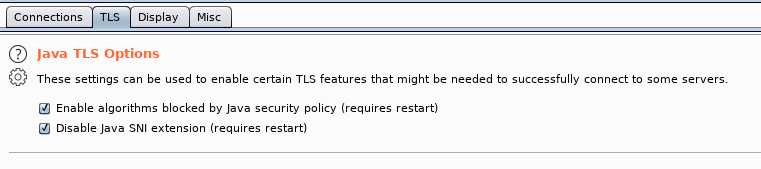
On the TLS tab, I enable both Java TLS options by default. When things go wrong with Burp, these are the first to be disabled.
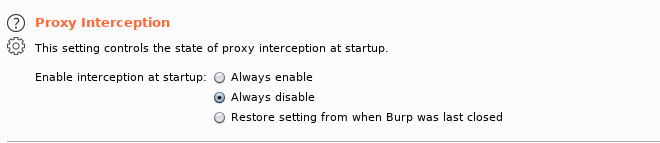
Make sure to disable proxy interception at startup so you don't go crazy.
Note: User options sometimes need to be reloaded for whatever reason. If burp is acting weird or your extensions didn't load, load them from the file menu.
Extensions
Make sure you use both Jython and JRuby to get access to all the burp extensions.
My favorite shortlist of extensions (though I'm probably missing some as I experiment with new ones and swap configs all the time).
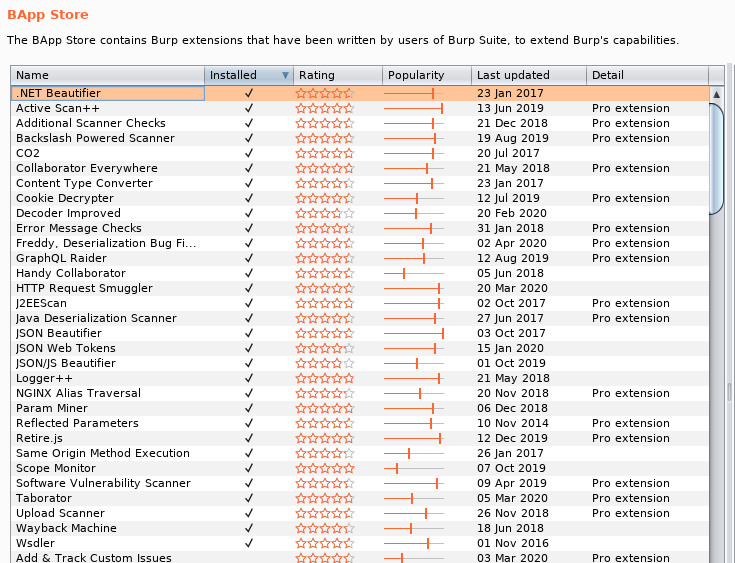
As you learn more about your target add additional extensions into your assessment.
Logger++
Make sure logger++ is the very last extension loaded otherwise it will miss some of the extensions traffic.
Additionally, change the maximum log entries to a larger result or you will be very sad when you forget and have to redo 20,000 requests :(
Decoder Improved
I love decoder improved, but don't use it for XXE payloads as it handles nested XML poorly. Might take a look at the source code for it one day.
Collaborator Everywhere
Great extension but if the app starts breaking you may need to switch it back to "Collaborator Nowhere".
Launcher
I tend to give burpsuite an extra couple gigs of ram because Java.
java -Xmx4098m -jar burpsuite_pro.jar
Troubleshooting
- Why is Burp not working? It's probably the TLS options. Or you have intercept on by default. Or collaborator everywhere is breaking the app.
- Why did my extensions disappear? Your default options loaded most likely don't point to the correct Jython/Jruby instances.
